Using SSH through AWS Session Manager
18 April 2020
We are planning to use AWS for our Java applications which is a step forward from the dedicated hosting that we currently have. Being on a corporate world, security is pretty tight and common ports are locked down including SSH port. This is a challenge since I have to SCP to deploy my jar and war files.
Luckily AWS allows to tunnel SSH through their session manager. I followed this guide to setup my connection. There are prerequisites to comply with and you need to have the correct role provisioned to your AWS login.
SSH connections through Session Manager checklist
- SSH is running on the instance (with inbound ports closed)
sudo netstat -tlnp | grep 22
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1056/sshd
tcp6 0 0 :::22 :::* LISTEN 1056/sshd
- SSM agent version 2.3.672.0 or higher is installed on the instance. You can view this using AWS System Manager > Session Manager or
sudo yum info amazon-ssm-agent
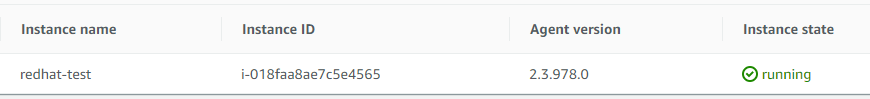
- Session manager plugin is installed on my local machine with version 1.1.23.0 or later
You can download session manager plugin from this link. This is an addon to your AWS CLI which you can install using choco install awscli. You can verify you have it by running
$ session-manager-plugin --version
1.1.61.0
- Add this to your SSH configuration typically at
~/.ssh/config
I'm sadly running git bash on Windows so I have the first configuration. If you are on *nix, please use the next one.
# SSH over Session Manager
host i-* mi-*
ProxyCommand /C/Windows/System32/WindowsPowerShell/v1.0/powershell.exe "aws ssm start-session --target %h --document-na
me AWS-StartSSHSession --parameters portNumber=%p"
# SSH over Session Manager
host i-* mi-*
ProxyCommand sh -c "aws ssm start-session --target %h --document-name AWS-StartSSHSession --parameters 'portNumber=%p'"
- Check if you have ssm:StartSession permission. Please check your IAM policy for this. On mine, it's attached to a custom SSMUserGroup with attached policy
AmazonSSMFullAccess.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "ssm:StartSession",
"Resource": [
"arn:aws:ec2:*:*:instance/instance-id",
"arn:aws:ssm:region:account-id:document/AWS-StartSSHSession"
]
}
]
}
- Configure your AWS CLI. You should ask your Administrator for your access Key ID and secret.
$ aws configure
AWS Access Key ID [****************N6EQ]:
AWS Secret Access Key [****************ffMZ]:
Default region name [eu-west-2]:
Default output format [json]:
Once configured, run aws ec2 describe-instances. You should see a long JSON describing your EC2 instance.
Testing your SSH console
Make sure you have downloaded the PEM file you created while launching the Amazon EC2 instance.
$ ssh -i Downloads/aws/redhat-free-tier.pem ec2-user@i-018faa8ae7c5e4565
This system is not registered to Red Hat Insights. See https://cloud.redhat.com/
To register this system, run: insights-client --register
Last login: Fri Apr 17 19:02:01 2020 from ::1
[ec2-user@ip-172-31-22-128 ~]$
To prove that port 22 is close, I run nmap and telnet against my EC2 instance.
$ nmap -Pn ec2-35-177-254-212.eu-west-2.compute.amazonaws.com
Starting Nmap 6.40 ( http://nmap.org ) at 2020-04-17 19:43 BST
Nmap scan report for ec2-35-177-254-212.eu-west-2.compute.amazonaws.com (35.177.254.212)
Host is up (0.013s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE
8080/tcp closed http-proxy
$ telnet ec2-35-177-254-212.eu-west-2.compute.amazonaws.com 22
Trying 35.177.254.212...
telnet: connect to address 35.177.254.212: Connection timed out